It's no secret that SaaS tools are becoming increasingly popular. Customers love them for a variety of reasons, from ease of use to affordability.
Unfortunately, this increased popularity also leads to an increased risk of data security risks. Data breaches can have serious consequences for SaaS companies, such as loss of customer trust and legal problems.
In this blog post, we discuss some practical strategies you can use to protect your SaaS business from data security risks.
Common Causes of SaaS Data Security Risks
Before you start looking at how to protect your organization from data breaches, it makes sense to first look at the most common causes of data breaches. Simply put, if you know the causes of data breaches, you know how to prevent them.
Weak Passwords
Weak passwords are arguably the leading cause of data breaches. In fact, 75% of Americans find it difficult to use strong passwords. Of those, about 24% still use common passwords. Even when asked to update their passwords, only 49% make minimal changes.
To give you an idea of how important strong passwords are, it only takes hackers about two seconds on average to crack an 11-digit password that contains only numbers.
Phishing Scams, Malware, and Ransomware
Other common causes of data breaches for SaaS businesses include phishing, malware, and ransomware attacks.
In phishing, cybercriminals entice victims to disclose personal or business information in emails that often appeal to urgency or the desire to make a profit.
For example, a person might receive an email from PayPal informing them that something is wrong with their account, and they need to log in to fix the problem. They then click on a fraudulent link in the email that takes them to a page where they enter their login credentials. This way, they give their PayPal account details to the criminals.
Malware attacks, in turn, occur when cybercriminals use malicious software to penetrate an organization's system or network. Ransomware is similar to malware, but it locks users out of their data or system until a ransom is paid. Similar to fishing, fraudulent emails trick recipients into clicking on attachments, which then install malware on their system.
Vigilance is critical when preventing these attacks. It’s essential to:
- Check senders’ email addresses.
- Avoid opening files or clicking on links sent by unknown senders.
- Investigate URLs before clicking on them.
- Avoid untrusted websites.
App Vulnerabilities
SaaS data security risks frequently occur as a result of unpatched vulnerabilities, too. You can almost think of these vulnerabilities as open doors that give hackers access to a system. Cybercriminals can exploit these to steal personal and company data such as names, emails, bank details, and customer information.
Incorrect Permission Management
Data breaches can happen if the wrong people have access to the wrong data. To prevent incidents, limit access to your business's data by using proper permission management. Monitor who accesses your systems, where they go, and what they take.
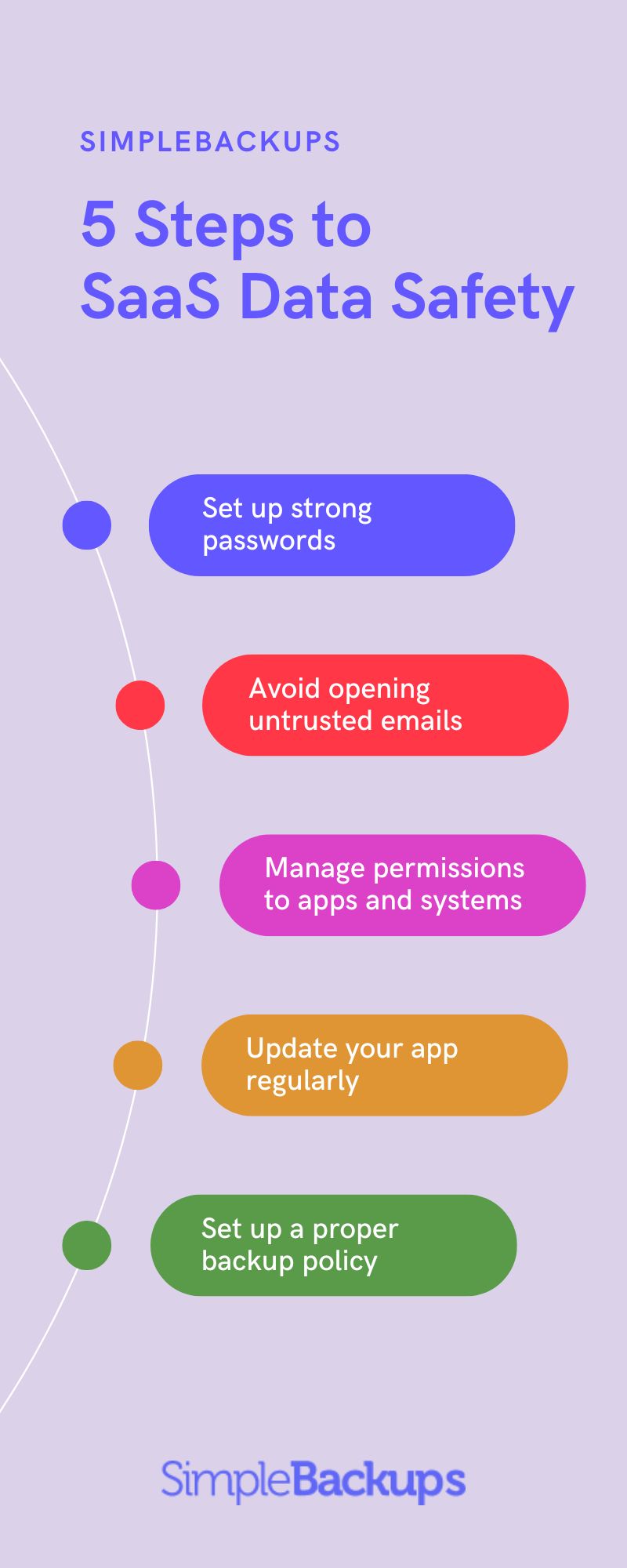
Best Practices to Prevent SaaS Data Security Risks
Now that you understand some of the common culprits, it’s time to look at the best practices you can use to keep yourself and your business safe.
Strong Passwords and Multifactor Authentication
One of the best ways to prevent data breaches is to ensure your employees and team use strong passwords. Cybersecurity experts agree that using different cases, numbers, and even special characters, in a single sentence is sufficient for a strong password.
Using a single word, on the other hand, isn't recommended as it could easily be associated with your personal information. If it's a challenge for your team to keep track of their passwords, investing in a reliable password manager could be a sensible solution.
Another way to prevent data breaches is to use multifactor authentication. This requires users to provide two or more pieces of information to confirm their identity (usually a password and a unique code sent to their phone). This method makes it more difficult for hackers and other criminals to gain access to sensitive data.
Regular Software Updates and Patches
Since app security vulnerabilities often lead to data breaches, it's in your best interest to prevent them. That's why regular software updates and patches are so important. They fix security holes and bugs in the software and make it difficult for hackers to exploit vulnerabilities.
Software updates also introduce new features and improvements that increase the performance and functionality of the software. In summary, this means that regular updates should be an integral part of your IT security strategy.
Employee Education and Training
As you may have noticed, many data breaches are caused by phishing and malware. This means that your employees are a major vulnerability when it comes to data breaches. To prevent such incidents, employee training is critical. Teach them how to recognize suspicious emails, files, and bad actor behavior and avoid becoming victims.
But training has another benefit: it creates a culture of cybersecurity. All of your employees are aware of the risks and are committed to protecting your company's data. This can help prevent cybersecurity incidents and ensure your company is well positioned to thrive in today's digital landscape.
Incident Response Plan
While the above strategies can minimize risk and prevent data breaches to some degree, they'll never be 100% effective. Nevertheless, data breaches will occur from time to time. This is where your incident response plan comes into play.
It outlines the steps you'll take when a data breach occurs and how you'll mitigate the damage after the breach.
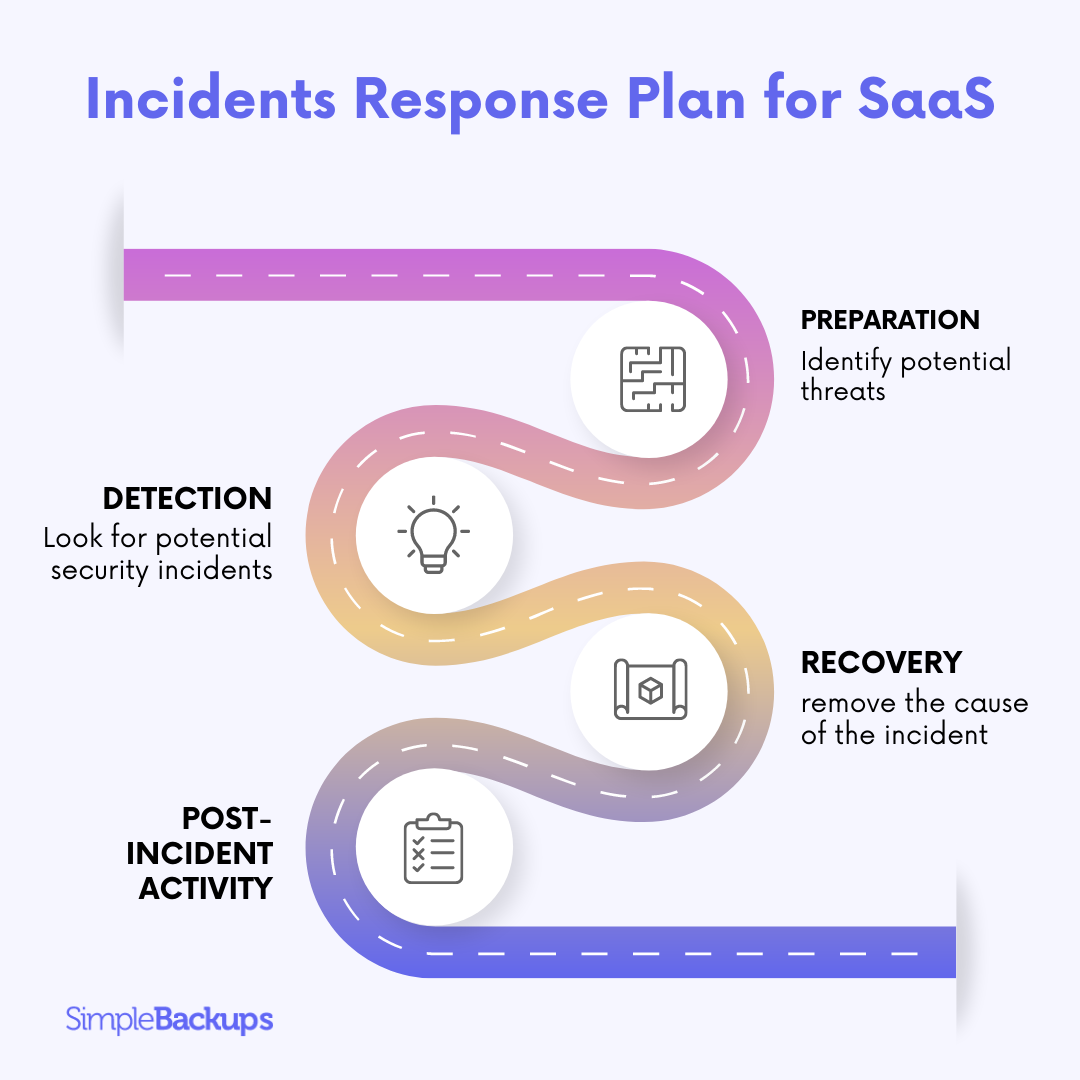
Typically, these will be the key elements of your incident response plan:
- Preparation: During the first step, you’ll conduct a risk assessment, identify potential threats and vulnerabilities, and create an incident response team. Your response team will generally include team members from different departments, and the plan will define the roles and responsibilities of each team member.
- Detection and Analysis: This involves monitoring your systems and networks for potential security incidents. Your plan will identify tools, platforms, and techniques that you’ll use to detect and analyze incidents. It should also set out the criteria for determining the severity of an incident.
- Containment, Eradication, and Recovery: This part of your plan revolves around what happens when an incident is identified. As such, it will determine what your team will do to contain the incident to prevent it from spreading, remove the cause of the incident, and recover from the subsequent damage. Your plan will detail the processes during each of these steps.
- Post-Incident Activity: You should also plan what will happen after the incident. This typically involves conducting a post-incident review to identify the vulnerabilities that led to the incident and how to eliminate them. This process will also help you identify areas where you can update and improve your response plan.
In the end, having a well-thought-out incident response plan helps you identify incidents quicker and more effectively while, at the same time, allowing you to recover faster.
Conclusion: Prevention Is Better than Cure
Today, it's extremely important to know how to protect your SaaS business from data breaches and how to respond and recover from a breach. One of the easiest ways to protect yourself is to create regular and consistent backups. That's where SimpleBackups comes in. We provide you with an all-in-one solution to ensure your data stays safe. To learn more about SimpleBackups and how it can help you, get started with your first backup today.